Building a Secure Industrial Edge: Serial Device Servers Design and Deployment Insights
1/06/2025
IEC 62443-4-2: A Global Benchmark for Industrial Cybersecurity
• IEC 62443-4-2 sets forth comprehensive cybersecurity technical requirements for Industrial Automation and Control Systems (IACS).
• For edge connectivity devices—Serial Device Servers and Protocol Gateways—IEC 62443-4-2 plays a particularly critical role. These edge components often act as the bridge between legacy industrial equipment and modern networks. As such, they are exposed to both IT and OT attack vectors. By ensuring that these devices comply with IEC 62443-4-2, organizations can significantly reduce their cybersecurity risk at one of the most vulnerable layers of the industrial stack.
• Incorporating IEC 62443-4-2-compliant edge devices is no longer optional—it's a strategic necessity for building secure, modern industrial environments.
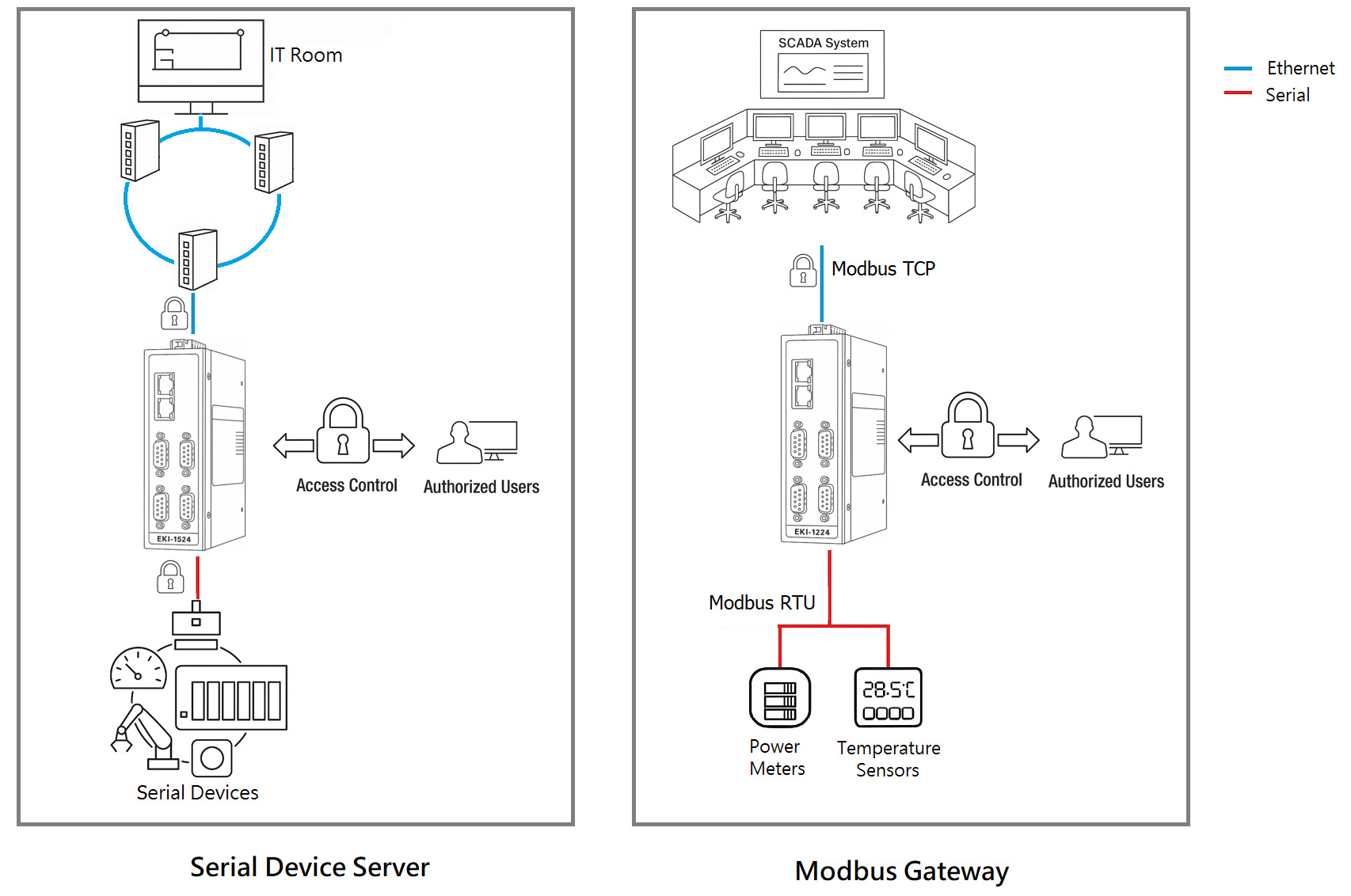
Security-Enhanced Architecture for Safe and Secure Deployment
l User Authentication and Authorization
Device access security and permission control are ensured through strong password policies, managed through authentication servers and assignment of customized privileges to different users. These meansures help prevent unauthorized access and enhance overall security.
l Secure Device Integrity
To ensure the integrity of edge connectivity devices, the product automatically performs SHA-256 verification before executing any firmware updates.
l Secure Deployment
Secure edge connectivity is achieved by disabling unnecessary services to enhance security and prevent unauthorized access.
l Secure Communication
Secure communication is implemented through encrypted protocols, using TLS 1.3 and HTTPS for secure connections, and SNMPv3 for secure network management.
l Access Control
The Accessible Serial Port IP List allows users to define trusted IP addresses permitted to access serial ports, enhancing security by blocking unauthorized connections.
EKIG Product Aligns with IEC 62443-4-2
| Products | EKI-122x/EKI-152x (1/2/4 Port) |
EKI-1526x-D (Coming Soon) |
| Security Functions for Secure Deployment | ||
| User Authentication and Authorization | Password protection (length, character enforcement) Authentication servers (RADIUS/LDAP) Customized privilege for different users |
Password protection (length, character enforcement) Authentication servers (RADIUS/LDAP) Customized privilege for different users |
| Secure Device Integrity |
Check SHA code before updating the device |
|
| Secure Deployment | Technical Documents Unused services can be disabled Disabled the default setting of the Telnet/SSH console |
Technical Documents
Unused services can be disabled Disabled the default setting of the Telnet/SSH console |
| Secure Communication | HTTPS (TLS 1.3 self-signed certificate, also supports public certificate import), SNMPv3 |
HTTPS (TLS 1.3 self-signed certificate, also supports public certificate import), SNMPv3 |
| Access Control | Accessible Serial Port IP List |
|
| Securing Your Devices with Efficient Maintenance | ||
| Configuration Management | WebGUI |
WebGUI |
| Device Management | Syslog (remote logging) |
Syslog (remote logging) |
| Vulnerability Management | Regularly update firmware and patch CVE vulnerabilities. |
|
| * Exclude EKI-1211/1511 and EKI-1526(8)x-CE/EKI-1528x-DR series products
** EKI-1526x-D CPU support security boot |
||

/EKI-1524_Front _S20180209105903.jpg)
/EKI-1221_Front right _S20180125181744.jpg)
/EKI-1222 _S20180125183153.jpg)
/EKI-1224 _S20180125185011.jpg)
/EKI-1522_Front left _S20180209104616.jpg)



